Online Security: Abortion Edition
The recent decision by the US Supreme Court to overturn Roe v. Wade has sparked off a flurry of "how to stay safe online" articles about internet anonymity. Some of these are... better than others.
The recent decision by the US Supreme Court to overturn Roe v. Wade has sparked off a flurry of "how to stay safe online" articles about internet anonymity. Some of these are... better than others. Today we're going to work through an article from the Anchorage Daily News and see what is right, and what is, well, less right.
:quality(70)/cloudfront-us-east-1.images.arcpublishing.com/adn/7XZ7C76JPNCLZFJONPFWKLY6RU.jpg)
This will hopefully give you a deeper understanding of the recommendations in the article - and why they're recommended.
Recommendation 1: Limit who you tell
This recommendation is excellent. For the most part, dragnet surveillance - when the government (or someone else, but realistically the government) captures everything for later analysis - tends to be an overwhelming volume of data. The sheer volume makes it hard to identify violations before they happen. Following up on every single search for "abortion provider" (or any of the hundreds of variations), for example, is just not possible for a group with finite resources.
Instead, law enforcement (or counterinsurgency forces of any kind) rely on dragnet surveillance to provide a history once something has tipped them. Tipping is what you'd imagine it is - some information indicates that a particular person is worth focusing on. The tip moves you into the "take a harder look" category, at which point pulling up your surveillance history can build a pattern of searches, traffic, and more than can implicate you after the fact.
Tipping is the use of one intelligence discipline, asset, or sensor type to
cross-cue or initiate collection by another sensor.
– Commander's Handbook for Persistent Surveillance, USJFCOM
This isn't to say that humans are the only thing that can provide a tip to the police. Certain actions, caught on surveillance, could be enough to merit further attention - but it's hard to know what those might be until it's too late. A web search might be safe when calling an abortion provider isn't, but you won't know until you've done something to tip the police off, or learned from someone who has.
The lesson here: there are multiple levels of necessary security, and some actions - like someone telling the police about you - move you to a higher category. The problem is that frequently (not always!), any slip-ups or information disclosed earlier on can be exploited later down the line after a tip has been received. Searching for an abortion provider now might not be a problem - the police can't check in on every single person who does - but if something or someone later tips the police off, surveillance data from the past might suddenly become a problem for you.
An example from the Anchorage Daily News article sums this up nicely:
When someone goes to a health provider with medical issues related to an abortion, medical professionals can report them to the police, who can then seize their phones or computers. With a device in hand, police can just look through the browser and text messages directly.
The lesson: focus on staying entirely out of sight and under the radar. You can't avoid all surveillance - in today's world, it's just not possible - but you can blend in. It's much easier to blend in if nobody is looking for you. Once you're noticed, everything becomes much, much more difficult.
Recommendation 2: Chat on a secure, encrypted messaging app
This is good advice! However, the article gets the details wrong. It starts by talking about end-to-end encryption, which is a great focus - end-to-end encryption means that messages are fully encrypted at all points between the sending device and receiving device. Only the sender and recipient's devices have the ability to decrypt and read the messages. However, the article then immediately recommends iMessages with the caveat that "Apple has the key to decrypt iMessages that are backed up using its iCloud service." That's not end-to-end encryption! That means that law enforcement can compel Apple to decrypt your messages, defeating the whole point. True end-to-end encryption means the only way to read messages is to unlock either your phone, or the phone you're sending messages to.
You should use a secure messaging app with end-to-end encryption - such as Signal - but be very cautious about what counts as security. Check out the EFF's Surveillance Self-Defense tool guide for guidance on how to use Signal or (if you must) WhatsApp.
Recommendation 3: Protect your devices
Well, hard to argue with that. First off, always follow this golden rule:
That includes handing over your devices unless compelled to!
The other good advice here is to use a passcode instead of Face ID or Touch ID. It's currently an undecided issue whether cops and courts can force you to unlock your phone using your face or fingerprint, but what is decided is that they can't compel you to enter a passcode.
Recommendation 3: Browse the internet securely
This is where things start to go a little off the rails. It starts off well by noting two ways your browsing can be captured - either from your device, or when it's logged in-transit. Using incognito mode can help keep your computer itself clean, and more privacy-focused browsers and search engines such as Firefox and DuckDuckGo can reduce (but not eliminate!) what data is logged about your browsing by other parties.
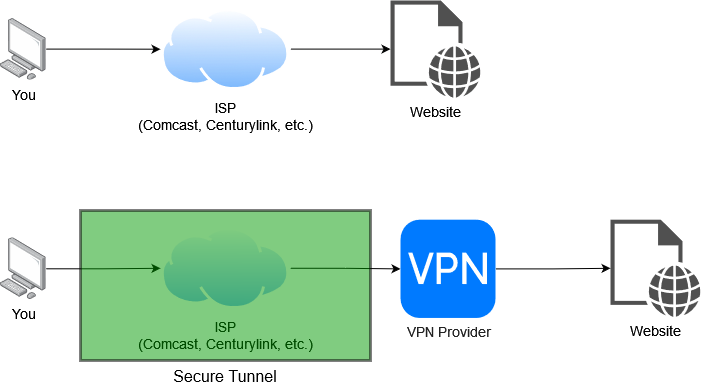
Unfortunately, this article follows a long-term trend of recommending VPNs without understanding their purpose. What a VPN does is essentially "move" you to a new place on the internet. Instead of traffic coming from your home to your internet service provider (ISP) and then to the website you're visiting, it goes to your home through your ISP while encrypted (so the ISP can't see anything about it), to the VPN provider, and then from there it's decrypted and sent to the website as usual.
To the website, your computer itself still looks the same - it can still detect what browser you're using, any cookies, details about your computer, and so on. Using a VPN changes three things:
- Your ISP can no longer view metadata about your traffic
- To the website, your computer is "at" the VPN provider - but still the same computer
- All of your traffic is now flowing through the VPN provider, so they can view metadata about it
This is, in many cases, not a useful change. VPN providers are still subject to subpoenas from law enforcement, and all of the data in your traffic - for instance, the details about your browser, what you click, any tracking cookies, and so on - is still there. A VPN doesn't change anything about your traffic itself, it just "relocates" it on the internet. Some VPN providers have a "no-log" certification claiming that they do not log any traffic, but they frequently still capture other data (such as when you use the VPN, the details of your account, and so on) that can be accessed by law enforcement. In some cases, the VPN even goes so far as to be actively tracking you, such as Facebook's Project Atlas.

For some users with a specific adversary in mind, a reputable VPN is helpful - if you live in a state where your ISP is required to report certain activities to the police (which, to my knowledge, isn't currently true anywhere) then using a VPN allows you to bypass that ISP and have your traffic "emerge" from a location elsewhere in the country or the world. But for most people, they don't make much sense.
The TOR Browser is a good "next step" if you're concerned, but it's a fairly technical tool that can be hard to use correctly. If you think it's necessary, you can learn about how to use TOR from the EFF. TOR establishes an anonymous connection to the internet, but like a VPN it doesn't remove any information contained in the traffic you send - think of it as sending a letter using an envelope without a return address, so it can't be traced back to you. If you sign your name on the letter (by logging in to your personal accounts using TOR, re-using a browser that you use for other things that can be fingerprinted, and so on), it doesn't matter that it was sent anonymously, since anyone reading the letter can see your name signed at the end.
Recommendation 4: Turn off location sharing, or leave your phone behind
This is in the right direction, but I think is missing some nuance. Turning off location services on your phone is a reasonable first step, but it will only protect you from parties who are purchasing and analyzing your data. There are also location tracking services (such as Apple's "Find My") that operate even if the phone is off. If you're worried about the police, leaving your phone at home is really the only reliable step.
The other two solutions mentioned - a faraday bag or a burner phone - are extremely difficult to get right. Faraday bags are difficult to build and evaluate, and they need to be used carefully - for instance, you need to put your phone in a faraday bag before you leave for any appointment, not once you arrive. It may also be the case that if you're later accused, your phone being "off the grid" for exactly the window of time you were alleged to be somewhere is considered to be suspicious. Simply leaving your phone at home makes it look more like you just were, well, at home. If you want extreme, nerdy detail about faraday bags, an article from Matt Blaze linked below does a great job.

As far as burner phones, they're even harder to use correctly. To stay truly secure, you'll need to buy the phone with cash, somewhere you won't be caught on camera or otherwise tracked doing it (you'll probably want to leave your phone at home, for instance). Once you have the burner, you can never use it at your home, work, or other frequent locations, you cannot use it to call any personal numbers (your own, your friends, family, etc.) and it can't be carried on you and trackable while you're carrying your other phone. Any of these things could give the police (if they looked hard enough - remember the first recommendation about staying under the radar) the ability to tie the phone to you.
It's much easier to just leave your phone at home.
Recommendation 5: Maximize your privacy settings
This won't hurt, but honestly I think it's a losing game. The whole point of social media companies is to collect as much data about you as possible. Having better privacy settings may prevent small amounts of data sharing here and there, but in the end you should assume anything you put on social media (including in private messages) will be disclosed. It's important to keep in mind that even if you don't say something directly, it can still be inferred. Something as benign as sending a message that says "hey I'm gonna be busy for a bit this afternoon, I can message you after" can become evidence for anyone trying to prove that you had a medical procedure on that day.
When in doubt, refer back to the video from the NLG earlier in this article.
Recommendation 6: Avoid period tracking apps
Yes. Assume anything you tell a company or organization will be disclosed to the government. (Ultimately, some will do it willingly and others can be subpoenaed, but if they operate in the US they are subject to the coercive powers of the US government.)
Recommendation 7: Limit where you share health information
Same as above. Even with the (somewhat) better legal privacy protections given to healthcare information through HIPAA, you should assume that information you disclose to any company or organization will be disclosed.
Recommendation 8: Be cognizant of physical surveillance technology
This is good advice, but nearly impossible to follow. Automated license plate readers dot most US cities - some for law enforcement, some for parking enforcement, some for tolls, some as part of red light cameras, and so on. Yet, at the same time, if you get on a public bus, it will certainly have interior cameras as well, and the transit card for paying the fare will log when and where you use it. Recall from earlier the difference between avoiding an active search (which will be nearly impossible) and staying under the radar.
Getting off the bus at a stop a few blocks from an abortion clinic isn't a red flag itself - there's no possible way that everyone who uses that bus stop could be investigated. But if you end up in court, suddenly someone who is looking for evidence may be able to use the fact that you got off at that stop at that time (and then back on the bus at a nearby stop later on after your appointment) as evidence to prosecute you. This is to reinforce the point that it's nearly impossible to truly escape an investigation - if the government decides they're going to find out about you, the only way to prevent that is to live an incredibly difficult and careful life and never slip up. For most of us, the key is to avoid suspicion, not to beat the government at their own game.
Conclusion
This is a lot. It's hard. That is, unfortunately, the point. Many, many people and billions of dollars work hard every year to make it this difficult. But you have one big advantage: you're part of a crowd. Focus on blending in, appearing normal to anyone who looks, and not doing anything that will raise a red flag and cause closer scrutiny, and you can disappear among all the other people living their lives.
There are many people out there fighting to make this easier for you and others - consider supporting them if you're able, even if (especially if) this doesn't impact you directly. They all need your help, whether that's your time, money, or voice (ideally, all of the above).
Some of the recommendations in the article we looked at today were great, and some less-so. If you'd like a well-researched article with security recommendations for those seeking an abortion, I highly recommend this one from the Electronic Frontier Foundation:

In general, the EFF is an amazing resource, and their Surveillance Self-Defense series is the gold standard for anyone who is interested in digging further.


