Counter-Network Operations and You
Introducing a short series on the use of social network analysis to understand and destroy underground groups.
Since the beginning of the Global War on Terror, research into social networks has been a hot topic within the US military. A well-known book within the field, "Networks and Netwars," published in November 2001, opens by describing this shift in focus:
The fight for the future makes daily headlines. Its battles are not between the armies of leading states, nor are its weapons the large, expensive tanks, planes, and fleets of regular armed forces. Rather, the combatants come from bomb-making terrorist groups like Osama bin Laden's al-Qaeda, drug smuggling cartels like those in Columbia and Mexico, and militant anarchists like the Black Bloc that ran amok during the Battle of Seattle.
To anyone who watches the military industrial complex today, these words from 2001 are a chilling primer on what the security state has become focused on in the decades since.
One of the largest shifts has been the change in how the military conceptualizes, maps, and understands its adversaries. Traditional military structures are hierarchical, and intelligence assets were focused on understanding the enemy's order of battle - the way that units were organized and deployed.
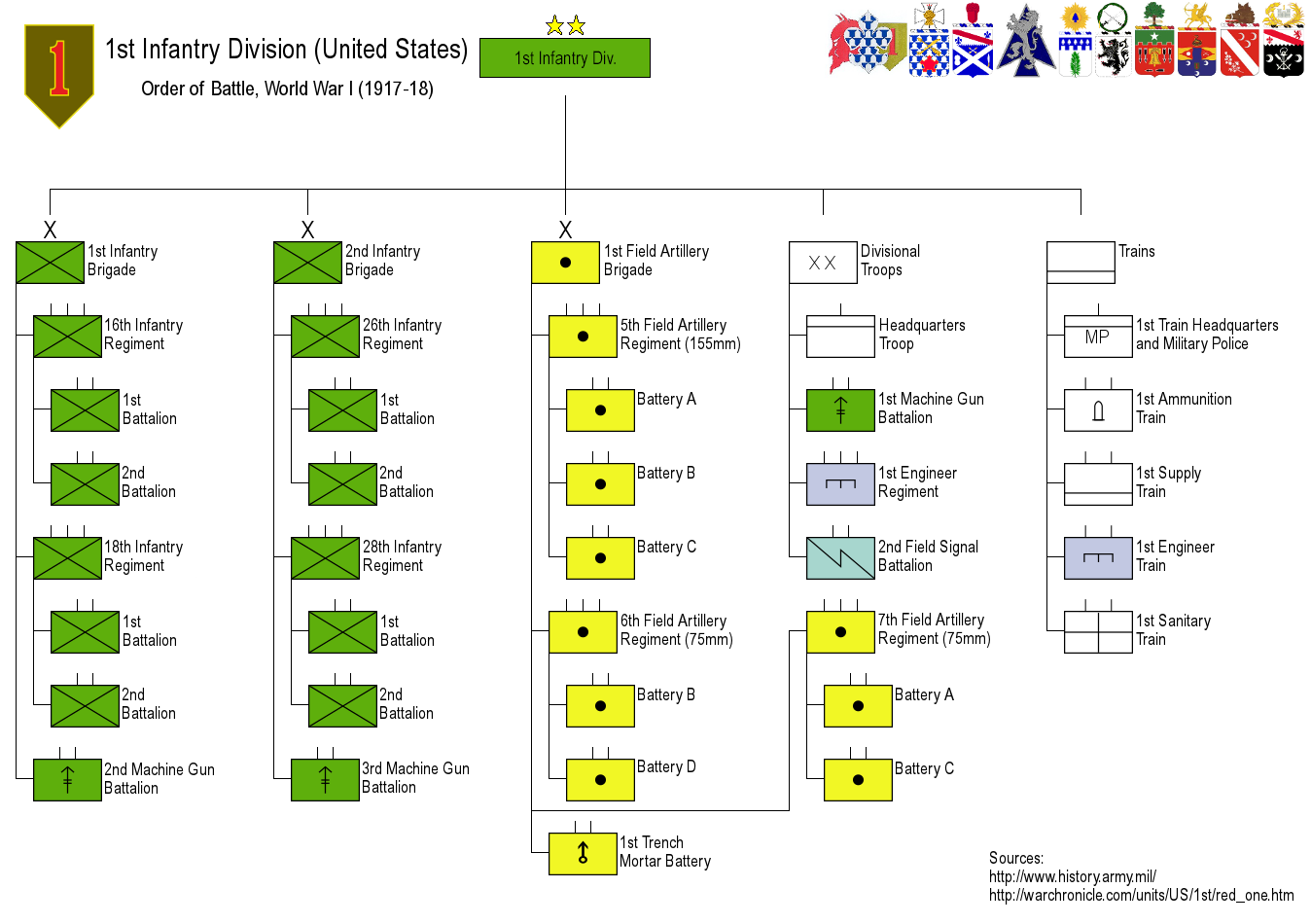
Examining the adversary this way helped a commander understand what they were likely to encounter in the field - both ahead of time to allow for planning, and in the thick of battle to allow anticipating the enemy's actions (if your troops are currently fighting the 1st Infantry Brigade, the odds are pretty good that the 2nd is nearby somewhere, and you should be ready for it).
The groups that the military has focused on for the past 20-odd years aren't organized in the traditional way, and order of battle analysis fell entirely flat. It was replaced, in time, with network analysis - the May 2014 updated version of FM 3-24, the Army's counterinsurgency manual, focuses heavily on "networked insurgencies." The emphasis on network analysis is clear:
For an insurgency, a network is not just a description of who is in the insurgent organization; it is a picture of the population, how it is put together and how members interact with one another.
By understanding these networks, the military can fight them, in the same way that understanding the order of battle allowed a commander to fight a traditionally organized enemy force. The activity of mapping a networked organization in order to destroy it became known as "counter-network operations." Learning about the way these operations are conceptualized and planned is key to understanding the operation of the modern security apparatus - from the military to federal, state, and local police forces. Thanks to the well-documented diffusion of knowledge and equipment from the military to domestic police, this understanding is applicable well beyond traditional counterinsurgency and increasingly relevant to our everyday lives.
Over the next couple of weeks, we'll be publishing a pair of articles about networked organizations and operations. We'll start with how networks are built and organizations are mapped, then follow with an article about how this information is used to destroy those organizations. Stay tuned!